September 3, 2025
On your phone, Apple or Google keep vulnerabilities in check. In the enterprise? You’re on your own.
Consumer tech has a safety net, app stores quietly map your apps, track versions, and push updates when vulnerabilities are found. Enterprises don’t have that luxury.
Inside an enterprise, the process usually starts with the NVD (the U.S. government–funded National Vulnerability Database). The NVD publishes Common Vulnerabilities and Exposures (CVEs). To connect CVEs to your own software, you need to use CPEs: special identifiers that represent software down to exact versions and sub-versions.
At scale it becomes a monumental task. Mapping your internal data against 1.4 million CPEs in the NVD is hard enough. Add in the complexity of product rebrands, mergers and acquisitions, inconsistent naming conventions, and multiple versioning schemes, and suddenly the problem becomes unmanageable. Our research shows this challenge is just as real for small software providers as it is for large enterprises.
Traditionally, organizations try to solve this through manual processes that are slow and error-prone. Entrio takes a different approach. We broke the problem into three parts:
We pull, transform, and manage our own version of all CPE names in the NVD database. This allows us better control over the data, improving speed, and accuracy for the next steps.
Once mapped, we can surface the CVEs relevant to your exact product versions, plus add context like CWE (vulnerability taxonomy), CVSS (severity scoring) as well as potential patches or vendor notes.

What used to take loads of manual effort is now an automated workflow. The result: faster, more accurate vulnerability intelligence, and more time for your team to focus on more strategic initiatives.
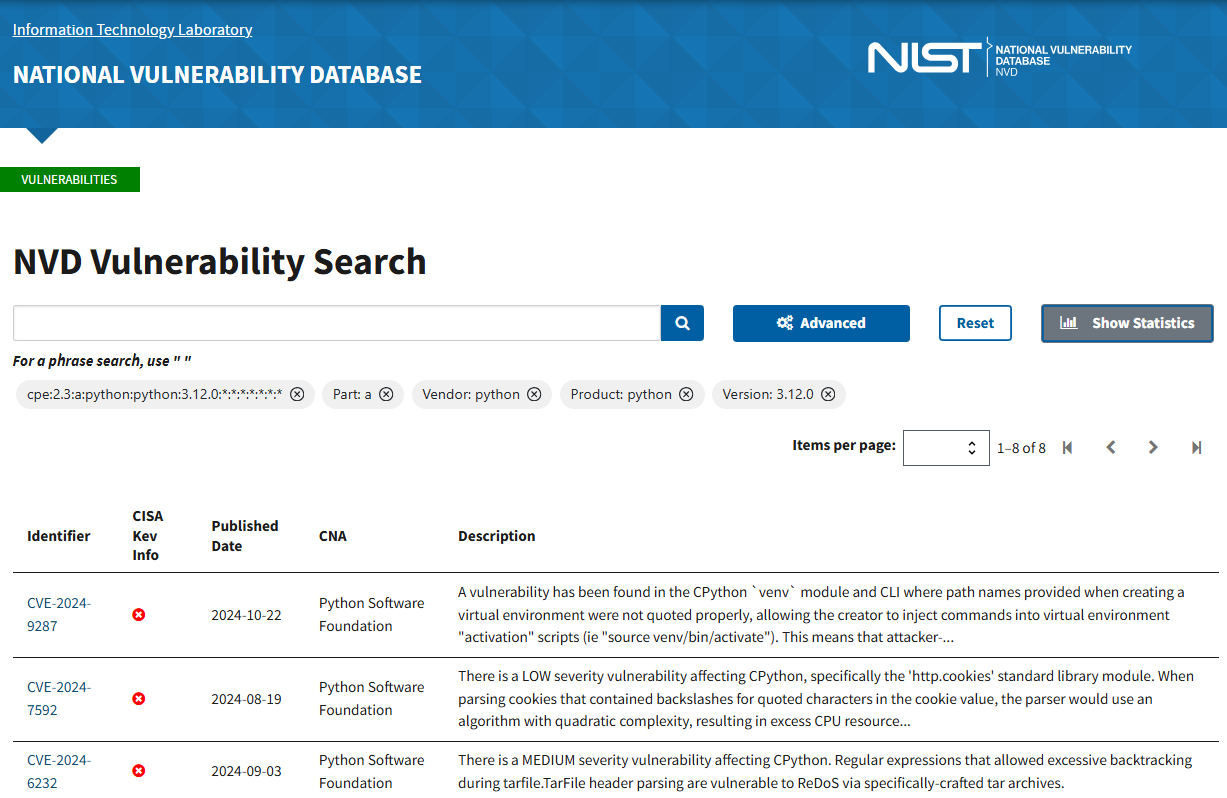
In our latest release, you’ll see links back to the NVD for associated CVEs. As the feature evolves, you’ll get richer outputs: CWE breakdowns, highlighted CVSS scores, curated reports powered by Gen AI, and more.
With Entrio, you move from reactive CVE chasing to proactive vulnerability governance, reducing risk, saving time, and giving your team full visibility.
